Information Gathering
You can use http://www.whois.com/whois website to get detailed information about a domain name information including its owner, its registrar, date of registration, expiry, name server, owner’s contact information, etc.
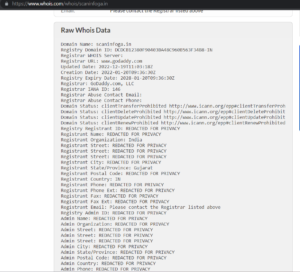
Here is a sample record of www.scaninfoga.inextracted from WHOIS Lookup −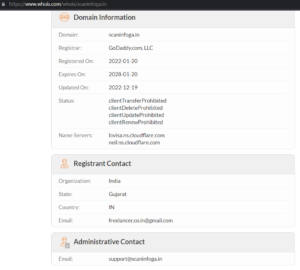
You can use ping command at your prompt. This command is available on Windows as well as on Linux OS. Following is the example to find out the IP address of scaninfoga.in
> ping scaninfoga.in
Pinging scaninfoga.in [172.67.211.78] with 32 bytes of data:
Reply from 172.67.211.78: bytes=32 time=173ms TTL=57
Reply from 172.67.211.78: bytes=32 time=176ms TTL=57
Reply from 172.67.211.78: bytes=32 time=179ms TTL=57
Reply from 172.67.211.78: bytes=32 time=172ms TTL=57Ping statistics for 172.67.211.78:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 172ms, Maximum = 179ms, Average = 175ms
Once you have the website address, you can get further detail by using ip2location.com website. Following is the example to find out the details of an IP address −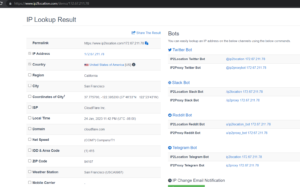
Here the ISP row gives you the detail about the hosting company because IP addresses are usually provided by hosting companies only.
Small sites may have a single IP address associated with them, but larger websites usually have multiple IP addresses serving different domains and sub-domains.
You can obtain a range of IP addresses assigned to a particular company using American Registry for Internet Numbers (ARIN).
You can enter company name in the highlighted search box to find out a list of all the assigned IP addresses to that company.
It is very easy to get a complete history of any website using www.archive.org.
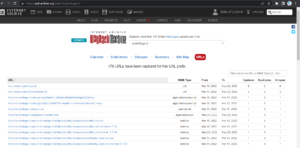
You can enter a domain name in the search box to find out how the website was looking at a given point of time and what were the pages available on the website on different dates.
Network scanning
a. -sL: List Scan – simply list targets to scan
b. -sn: Ping Scan – disable port scan
c. -Pn: Treat all hosts as online — skip host discovery
a. -sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/Window/Maimon scans
b. -sU: UDP Scan
c. -sN/sF/sX: TCP Null, FIN, and Xmas scans
d. –scanflags <flags>: Customize TCP scan flags
a. -p <port ranges>: Only scan specified ports
b. –exclude-ports <port ranges>: Exclude the specified ports from scanning
c. -F: Fast mode – Scan fewer ports than the default scan
a. -sV: Probe open ports to determine service/version info
a. -O: Enable OS detection
- nmap -v -A google.com
- nmap -v -sn 192.168.0.1-100
- nmap -v -O 192.168.1.200-210
- nmap -v -iR 10000 -Pn -p 443